双向数据绑定UML类图设计
面向对象设计第一步是设计类的继承结构和类的实例依赖组合关系,而最好的表达莫过于UML类图。
考虑一个支持数据双向绑定的GridView的设计,首先设计ViewModel的类继承和对象关系
以及View的类体系结构
最后处理双向绑定关系
面向对象设计第一步是设计类的继承结构和类的实例依赖组合关系,而最好的表达莫过于UML类图。
考虑一个支持数据双向绑定的GridView的设计,首先设计ViewModel的类继承和对象关系
以及View的类体系结构
最后处理双向绑定关系
传统的应用在处理错误时
响应式编程要求应用快速响应错误,并快速的自动恢复,不影响业务逻辑的正常运作。这要求将错误也作为一种事件抛出,交给Supervisor角色去异步处理,而正常的业务逻辑与Supervisor是分开的,不会受到影响。把错误作为一等国民对待,对错误建模,在应用设计过程中一开始就考虑错误处理。
有人吐槽面向对象设计过于复杂,只要Design by Contract,Prefer Composition over Inheritance,Loose Couple就可以了。我要说,这样的认识层次还不够高。这就好比,因为红学家把红楼梦整的特玄乎,而认为红楼梦本身不是好作品。
面向对象分析与设计,是一种方法论,是我们认识世界和改造世界的方法的理论。接口,继承,多态,SOLID等等都只是表象,我们需要做的是透过现象看到本质——那就是,不要从一开始就尝试去具体解决一个问题,或者实现一个需求,而是去描述一个问题,即建模。面向对象设计只是众多建模方式的一种,函数式编程以函数为中心建模,状态机以状态和变迁为中心建模,而面向对象以对象为中心建模则是最符合人们对客观世界的认识的。正如做人一样,有自己的世界观作为准则,做事的时候不必拘泥于具体的某个方法。
伴随移动设备的智能化,移动应用呈现出爆发式的增长。当应用多了以后,应用框架也就自然而然的提上日程。框架设计的第一步就是模块化,实现公共模块和应用模块,模块之间通过接口通信,然后才可能去更进一步的考虑依赖注入,MVC框架,领域和事件模型。Android在模块化方面继承了Java的特点,允许以jar包的方式组织和发布模块,不同的是Android必须将jar包打包进apk,不支持从ClassPath动态载入模块。
在Android模块依赖管理有两个经常遇见的问题:
最后,再强调一下,仔细的分析log,不能忽视任何警告和错误信息。
从面向过程到面向对象是一种思维方式的转变。面向过程是演绎思维,从一般到特殊,是由上而下的解决一个问题;而面向对象是归纳思维,从特殊到一般,是由下而上的描述一个问题
我们可以看到现代软件工程也是逐渐的从演绎向归纳变化:
LMAX disruptor is a high performance alternative to bounded queues for exchanging data between concurrent threads. Disruptor is first applied in financial and messaging systems for its high performance.
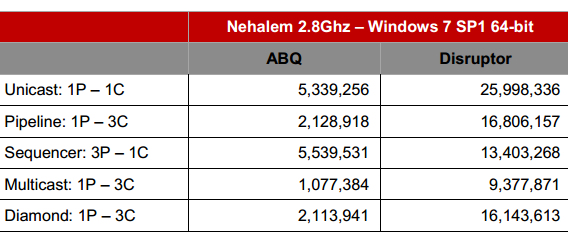
Disruptor throughput compared to queue
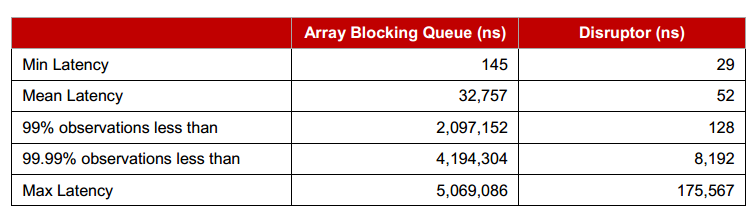
Latency compared to queue
Showing mechanical sympathy to modern CPU designs, disruptor is so fast in a parallel and staged environment. Following explains this in detail.
The best way to explain technology is by metaphor. As is said:
Technology is similar, thought behind is the key.
You are the boss of a fast food restaurant, what are you supposed to do to serve more customers? You hire a waitress with fast hands.
Waitress with fast hands

However the speed of waitress is limited, so you hire another waitress. Now the two process requests in parallel, and total throughput is doubled.
Hire two waitresses
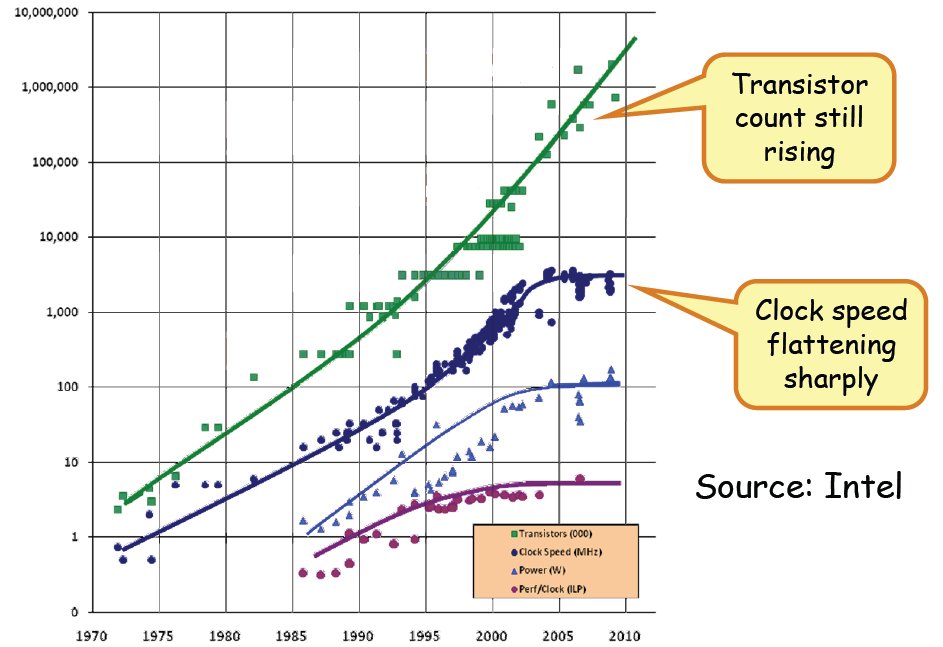
Parallel programming is just the same. with a high speed CPU, programs can run fast, result in high throughput and low latency. However CPU speed is limited to several GHZ, so more CPU cores are introduced, and programs can run in parallel.
CPU speed is limited, but the core numbers obey Moore’s law
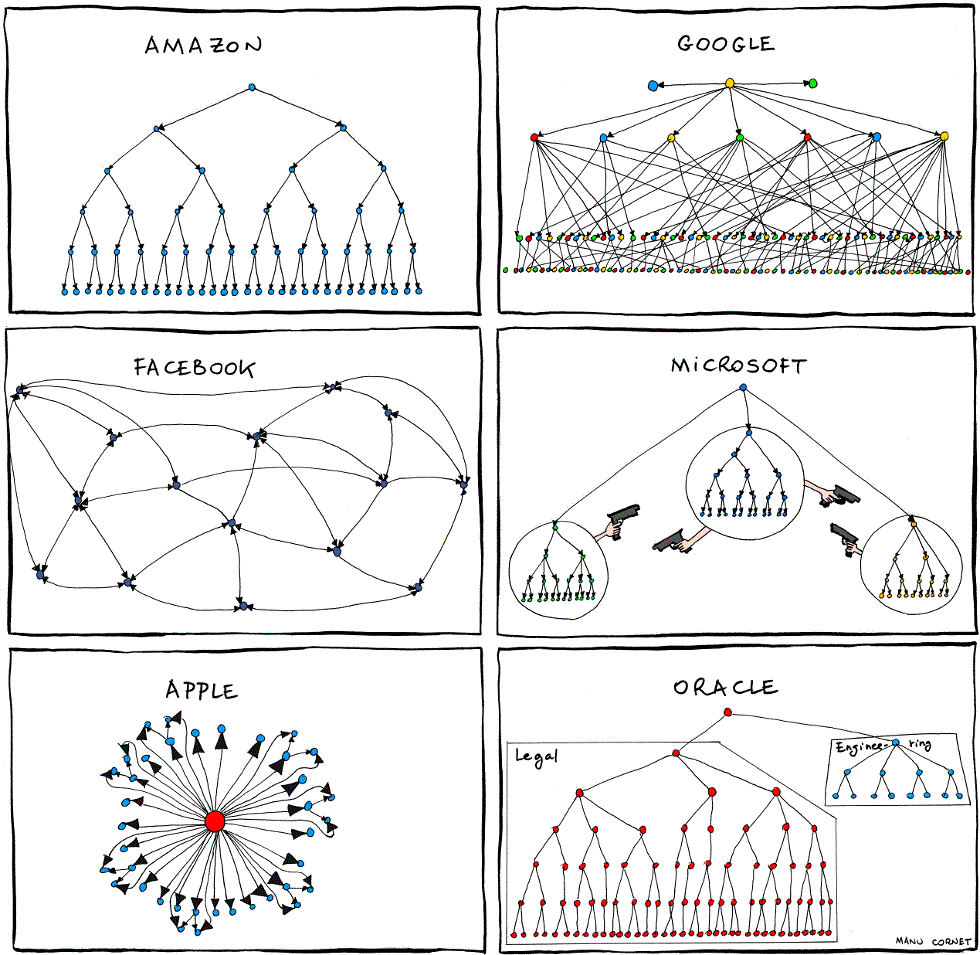
Your restaurant grows rapidly, so you must extend your business to more cities, even more countries. As the boss you can not manage all of your employee by yourself, instead you hire managers.
an organization is composed of multiple stages
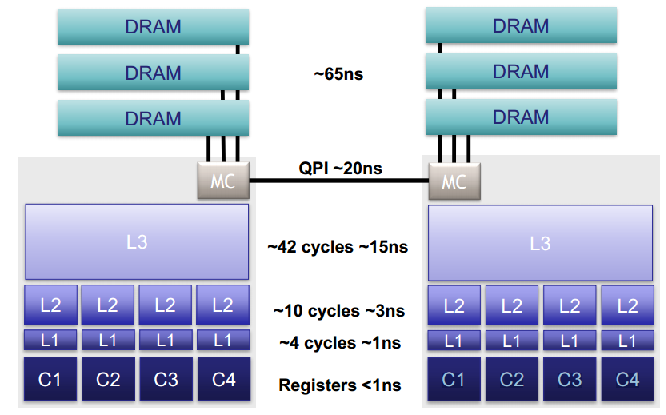
Modern CPU has multiple level caches, and the architecture is similar to an organization.
CPU cache contains multiple stages
In real world there is all kind of inefficiency, one department may depend on another. That’s why management theories exists.
In a program, how can we optimize process in such a parallel and staged environment?
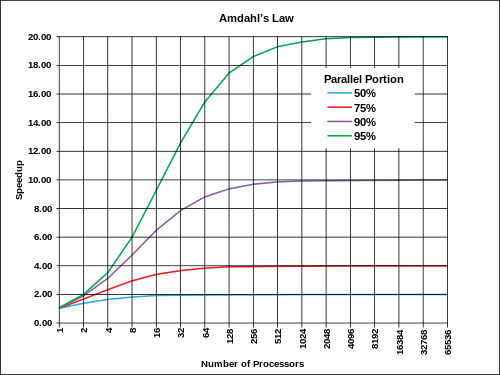
Amdahl’s law
The speedup of a program using multiple processors in parallel computing is limited by the time needed for the sequential fraction of the program. If %5 of the program cannot compute in parallel, the speedup can only reach 20 times no matter how many processors there are.
Amdahl’s law
To remove inefficiency, just find the bottleneck that can not run in parallel, namely avoid shared resources.
The first bottleneck is main memory access, which is expensive.
Manager collect status of employees, but they do not send to the boss you one by one, instead they wait until all the status are collected, and send to you in a batch.
Similarly, CPU cache is split to cache lines, and batch read data from main memory.
Disruptor use ring buffer to place objects padding together in memory so as to avoid false sharing and cache miss.
Ring buffer
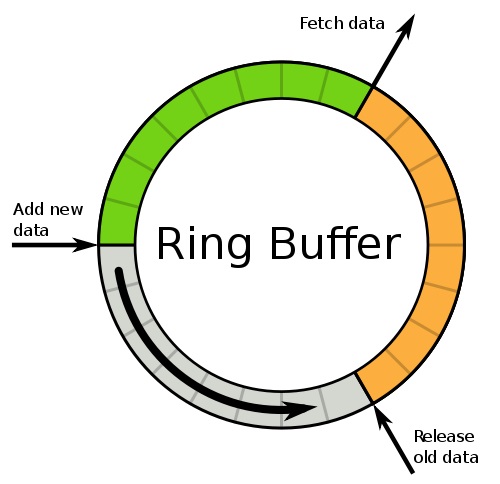
Another bottleneck is shared locks.
People manager and product manager both manage employees. They can exchange status of employees directly since their offices are close to each other.
Synchronization for shared resource is expensive.
lock penalty
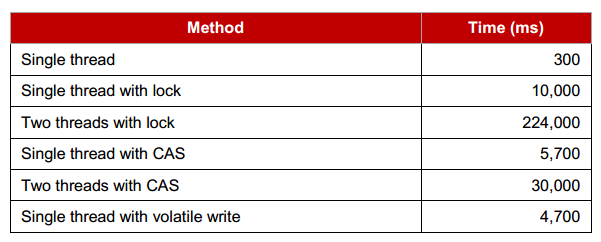
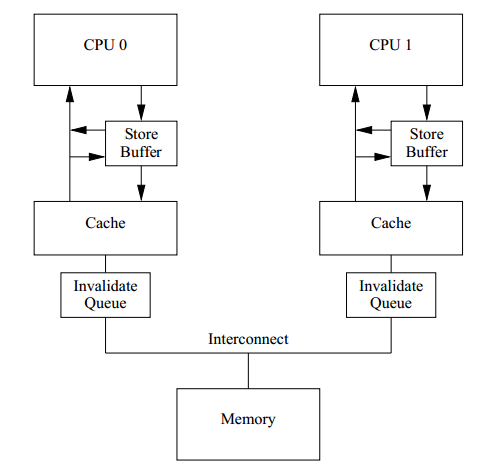
Disruptor use lock free memory barrier to synchronize sequence of ring buffer. Two cores in CPU talk to each other directly via memory barrier to exchange resource state, so as to avoid accessing shared locks.
memory barrier